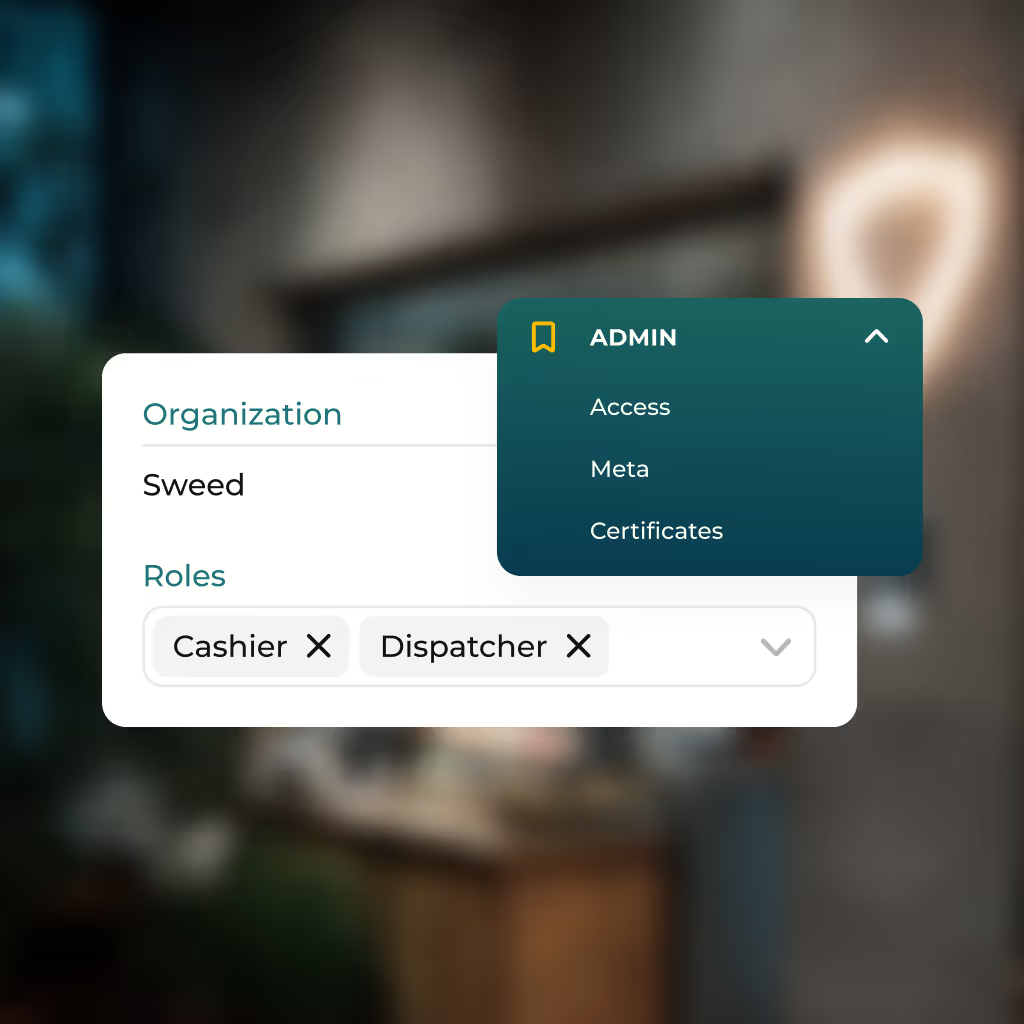
Access Control
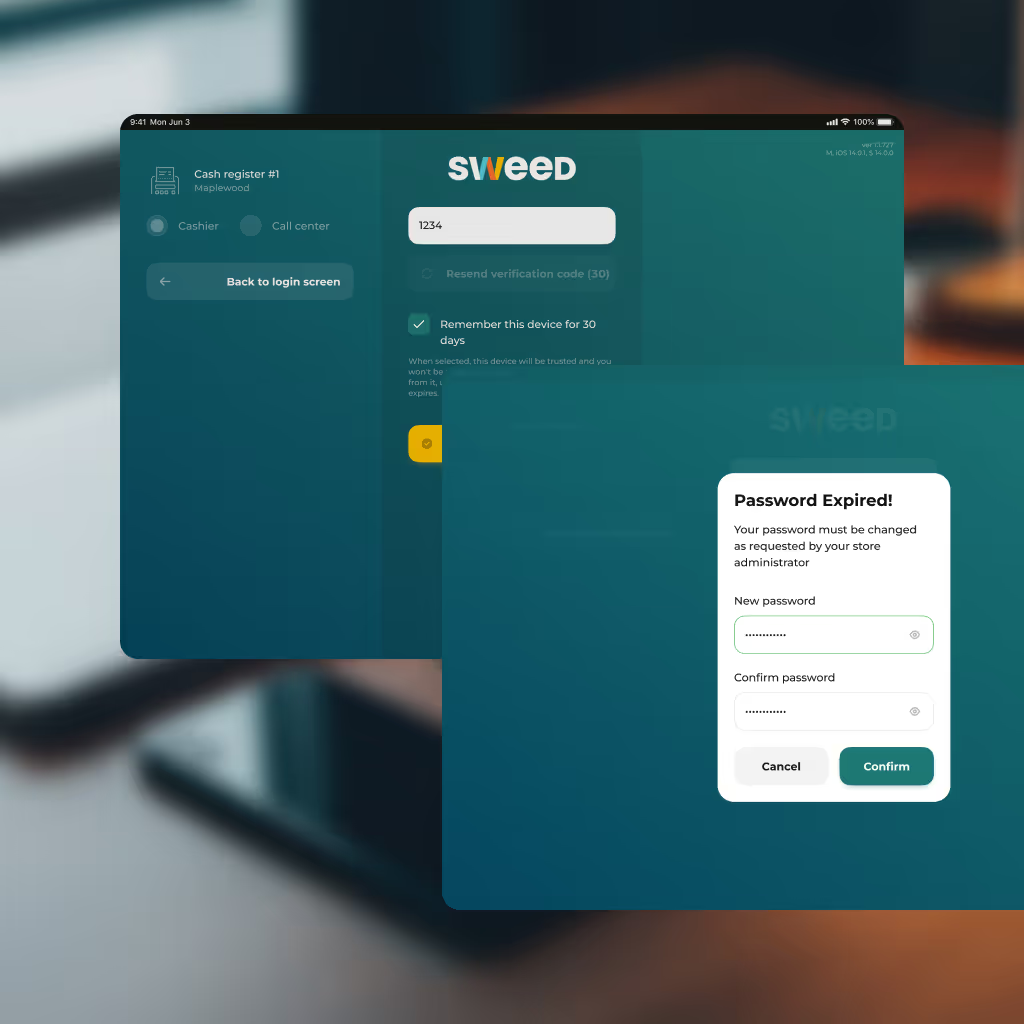
User access is secured through strict authentication and permission management tailored to cannabis retail environments. All accounts require passwords and mandatory two-factor authentication (2FA).
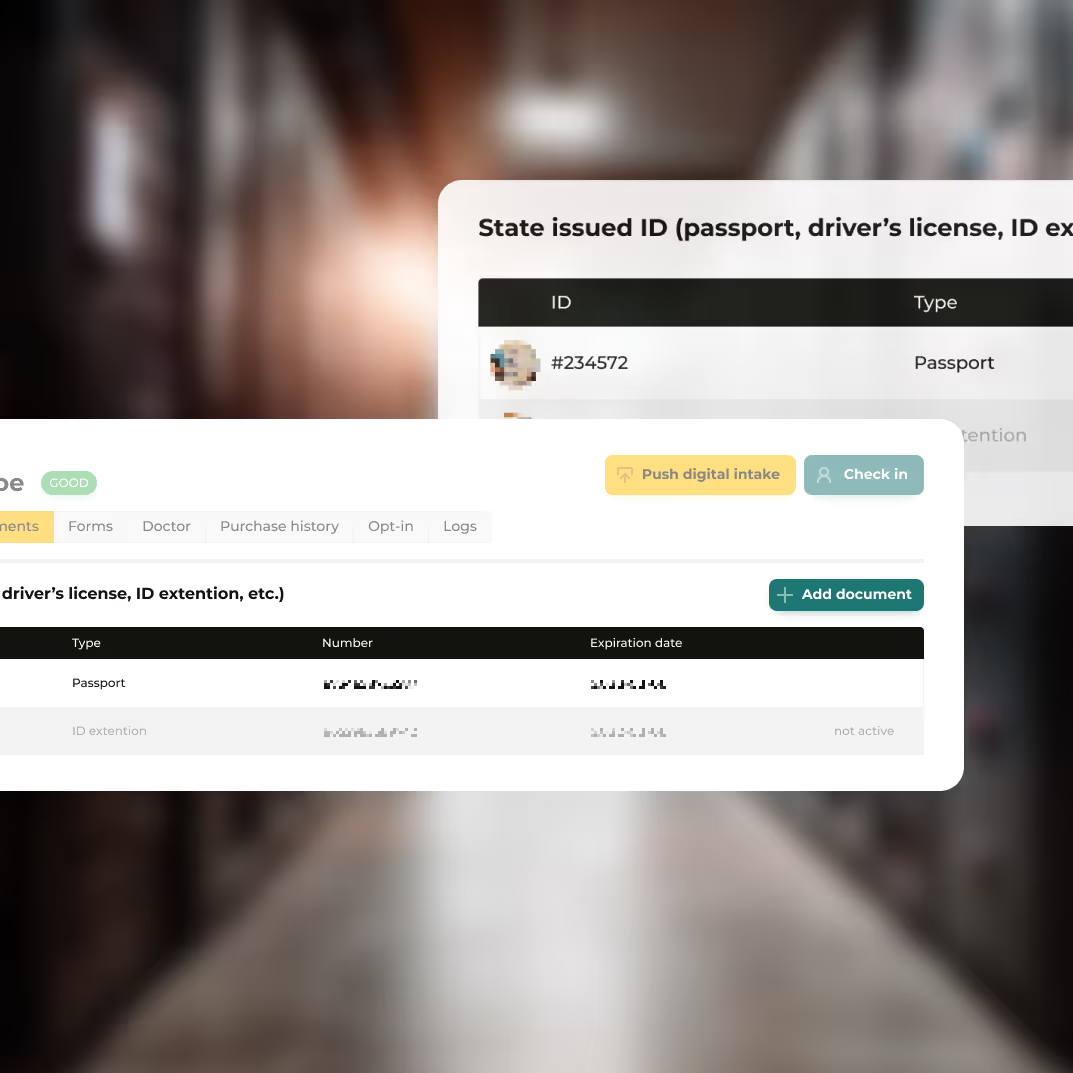
Role-based access control (RBAC) ensures users only access the cannabis inventory, sales, or compliance tools appropriate for their role. Routine audits help maintain least-privilege standards.






%201.svg)